Seleksi ITNSA SMKN 2 Depok Sleman

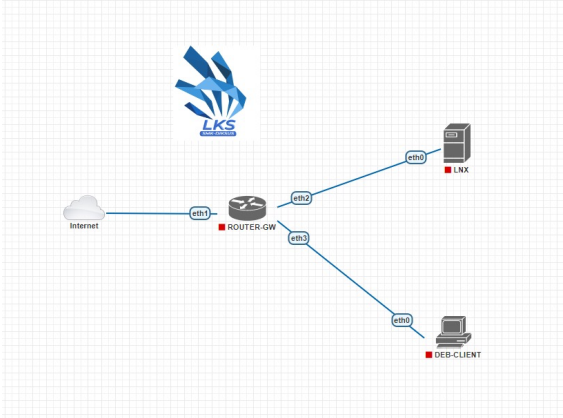
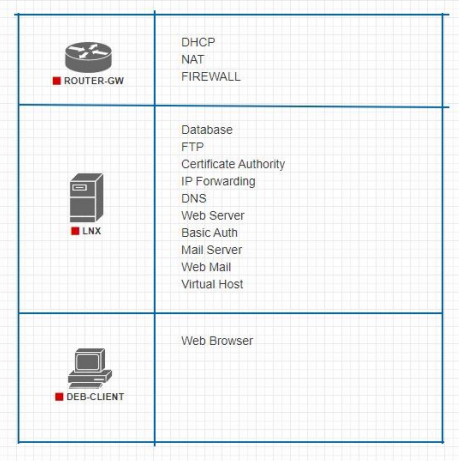
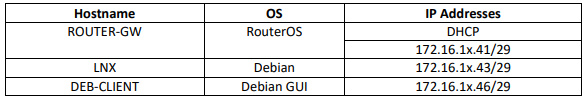
ROUTER-GW
Ganti password admin dengan Skills39
passwordGanti hostname router
/system identity set name=ROUTER-GWRenew license
/system license generate-new-id/system license renewAktifkan DHCP client pada ether1 (opsional)
/ip dhcp-client add interface=ether1 disabled=noTambahkan firewall NAT
/ip firewall nat add chain=srcnat action=masquerade out-interface=ether1Tambahkan ip pada ether2
/ip address add interface=ether2 address=172.16.18.41/29
LNX
Konfigurasi IP statis
sudo nano /etc/network/interfacesGanti enp0s3 menggunakan IP statis
# The primary network interface
allow-hotplug enp0s3
iface enp0s3 inet static
address 172.16.18.43/29
gateway 172.16.18.41
dns-nameservers 1.1.1.1/etc/network/interfaces
Ganti Hostname
sudo hostnamectl hostname LNXedit file /etc/hosts
127.0.0.1 localhost
172.16.18.41 LNX/etc/hosts
Edit file /etc/ssh/sshd_config
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/local/bin:/usr/bin:/bin:/usr/games
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
Include /etc/ssh/sshd_config.d/*.conf
Port 22
#AddressFamily any
ListenAddress 0.0.0.0
#ListenAddress ::
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_ecdsa_key
#HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
PermitRootLogin no
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# Expect .ssh/authorized_keys2 to be disregarded by default in future.
#AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication yes
#PermitEmptyPasswords no
# Change to yes to enable challenge-response passwords (beware issues with
# some PAM modules and threads)
KbdInteractiveAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the KbdInteractiveAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via KbdInteractiveAuthentication may bypass
# the setting of "PermitRootLogin prohibit-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and KbdInteractiveAuthentication to 'no'.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
PrintMotd no
#PrintLastLog yes
#TCPKeepAlive yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# Allow client to pass locale environment variables
AcceptEnv LANG LC_*
# override default of no subsystems
Subsystem sftp /usr/lib/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
/etc/ssh/sshd_config
FTP (vsftpd)
Install vsftpd
sudo apt update
sudo apt install ftp vsftpdBackup file konfigurasi
sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.backupBuat user competitor (jika belum ada)
sudo adduser competitorTambahkan user competitor ke userlist
sudo echo "competitor" | tee -a /etc/vsftpd.userlistBuat directory FTP
sudo mkdir /home/competitor/share
sudo chown competitor:competitor /home/competitor/shareKonfigurasi FTP
sudo nano /etc/vsftpd.confUbah beberapa baris berikut
listen=YES
listen_ipv6=NO
write_enable=YES
chroot_local_user=YES
# tambahkan dibawah chroot_local_user=YES
allow_writeable_chroot=YES
/etc/vsftpd.conf
Tambahkan di akhir
# User sub token
user_sub_token=$USER
local_root=/home/$USER/share
# FTP user list
userlist_enable=YES
userlist_file=/etc/vsftpd.userlist
userlist_deny=NO/etc/vsftpd.conf
Restart service vsftpd
sudo systemctl restart vsftpd.serviceDNS Server (Bind9)
Install bind9
sudo apt update
sudo apt install -y bind9Konfigurasi bind9
sudo cd /etc/bind
sudo cp db.local db.stembayo.id
sudo cp db.127 db.172.16.1xEdit file db.stembayo.id
;
; BIND data file for local loopback interface
;
$TTL 604800
@ IN SOA stembayo.id. root.stembayo.id. (
2 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS stembayo.id.
@ IN A 172.16.11.43
lnx IN A 172.16.11.43
mail IN A 172.16.11.43
basic-auth IN A 172.16.11.43
wordpress IN A 172.16.11.43
www.wordpress IN A 172.16.11.43db.stembayo.id
Edit file db.172.16.11
;
; BIND reverse data file for local loopback interface
;
$TTL 604800
@ IN SOA stembayo.id. root.stembayo.id. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS stembayo.id.
43 IN PTR stembayo.id.db.172.16.11
Edit file named.conf.local
//
// Do any local configuration here
//
// Consider adding the 1918 zones here, if they are not used in your
// organization
//include "/etc/bind/zones.rfc1918";
zone "stembayo.id" {
type master;
file "/etc/bind/db.stembayo.id";
};
zone "11.16.172.in-addr.arpa" {
type master;
file "/etc/bind/db.172.16.11";
};named.conf.local
Edit file named.conf.options
options {
directory "/var/cache/bind";
// If there is a firewall between you and nameservers you want
// to talk to, you may need to fix the firewall to allow multiple
// ports to talk. See http://www.kb.cert.org/vuls/id/800113
// If your ISP provided one or more IP addresses for stable
// nameservers, you probably want to use them as forwarders.
// Uncomment the following block, and insert the addresses replacing
// the all-0's placeholder.
forwarders {
1.1.1.1;
};
//========================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//========================================================================
dnssec-validation no;
listen-on-v6 { any; };
};named.conf.options
Restart bind9
sudo systemctl restart bind9Referensi: https://zonabiner.com/tutorial/debian/konfigurasi-dns
Certificate Authority & Wildcard SSL
Install easy-rsa
sudo apt update
sudo apt install easy-rsaPersiapan
mkdir /ssl
mkdir newcerts crl
cd /ssl
touch index.txt
echo 00 > serialBuat file openssl.cnf
#
# OpenSSL example configuration file.
# See doc/man5/config.pod for more info.
#
# This is mostly being used for generation of certificate requests,
# but may be used for auto loading of providers
# Note that you can include other files from the main configuration
# file using the .include directive.
#.include filename
# This definition stops the following lines choking if HOME isn't
# defined.
HOME = .
# Use this in order to automatically load providers.
openssl_conf = openssl_init
# Comment out the next line to ignore configuration errors
config_diagnostics = 1
# Extra OBJECT IDENTIFIER info:
# oid_file = $ENV::HOME/.oid
oid_section = new_oids
# To use this configuration file with the "-extfile" option of the
# "openssl x509" utility, name here the section containing the
# X.509v3 extensions to use:
# extensions =
# (Alternatively, use a configuration file that has only
# X.509v3 extensions in its main [= default] section.)
[ new_oids ]
# We can add new OIDs in here for use by 'ca', 'req' and 'ts'.
# Add a simple OID like this:
# testoid1=1.2.3.4
# Or use config file substitution like this:
# testoid2=${testoid1}.5.6
# Policies used by the TSA examples.
tsa_policy1 = 1.2.3.4.1
tsa_policy2 = 1.2.3.4.5.6
tsa_policy3 = 1.2.3.4.5.7
# For FIPS
# Optionally include a file that is generated by the OpenSSL fipsinstall
# application. This file contains configuration data required by the OpenSSL
# fips provider. It contains a named section e.g. [fips_sect] which is
# referenced from the [provider_sect] below.
# Refer to the OpenSSL security policy for more information.
# .include fipsmodule.cnf
[openssl_init]
# providers = provider_sect
# List of providers to load
# [provider_sect]
# default = default_sect
# The fips section name should match the section name inside the
# included fipsmodule.cnf.
# fips = fips_sect
# If no providers are activated explicitly, the default one is activated implicitly.
# See man 7 OSSL_PROVIDER-default for more details.
#
# If you add a section explicitly activating any other provider(s), you most
# probably need to explicitly activate the default provider, otherwise it
# becomes unavailable in openssl. As a consequence applications depending on
# OpenSSL may not work correctly which could lead to significant system
# problems including inability to remotely access the system.
# [default_sect]
# activate = 1
####################################################################
[ ca ]
default_ca = CA_default # The default ca section
####################################################################
[ CA_default ]
dir = /ssl # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several certs with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/ca.crt # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/ca.key # The private key
x509_extensions = usr_cert # The extensions to add to the cert
# Comment out the following two lines for the "traditional"
# (and highly broken) format.
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
# Extension copying option: use with caution.
# copy_extensions = copy
# Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs
# so this is commented out by default to leave a V1 CRL.
# crlnumber must also be commented out to leave a V1 CRL.
# crl_extensions = crl_ext
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = sha256 # use public key default MD
preserve = no # keep passed DN ordering
# A few difference way of specifying how similar the request should look
# For type CA, the listed attributes must be the same, and the optional
# and supplied fields are just that :-)
policy = policy_anything
# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
####################################################################
[ req ]
default_bits = 2048
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extensions to add to the self signed cert
# Passwords for private keys if not present they will be prompted for
# input_password = secret
# output_password = secret
# This sets a mask for permitted string types. There are several options.
# default: PrintableString, T61String, BMPString.
# pkix : PrintableString, BMPString (PKIX recommendation before 2004)
# utf8only: only UTF8Strings (PKIX recommendation after 2004).
# nombstr : PrintableString, T61String (no BMPStrings or UTF8Strings).
# MASK:XXXX a literal mask value.
# WARNING: ancient versions of Netscape crash on BMPStrings or UTF8Strings.
string_mask = utf8only
req_extensions = v3_req # The extensions to add to a certificate request
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = ID
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Daerah Istimewa Yogyakarta
localityName = Locality Name (eg, city)
localityName_default = Sleman
0.organizationName = Organization Name (eg, company)
0.organizationName_default = SMKN 2 Depok Sleman
# we can do this but it is not needed normally :-)
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = SMKN 2 Depok Sleman
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
emailAddress = Email Address
emailAddress_default = [email protected]
emailAddress_max = 64
# SET-ex3 = SET extension number 3
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 4
challengePassword_max = 20
unstructuredName = An optional company name
[ usr_cert ]
# These extensions are added when 'ca' signs a request.
# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.
basicConstraints=CA:FALSE
# This is typical in keyUsage for a client certificate.
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment
# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
# This stuff is for subjectAltName and issuerAltname.
# Import the email address.
# subjectAltName=email:copy
# An alternative to produce certificates that aren't
# deprecated according to PKIX.
# subjectAltName=email:move
# Copy subject details
# issuerAltName=issuer:copy
# This is required for TSA certificates.
# extendedKeyUsage = critical,timeStamping
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = DNS:stembayo.id,DNS:*.stembayo.id
# [ alt_names ]
# DNS.1 = stembayo.id
# DNS.2 = *.stembayo.id
[ v3_ca ]
# Extensions for a typical CA
# PKIX recommendation.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = critical,CA:true
# Key usage: this is typical for a CA certificate. However since it will
# prevent it being used as an test self-signed certificate it is best
# left out by default.
# keyUsage = cRLSign, keyCertSign
# Include email address in subject alt name: another PKIX recommendation
# subjectAltName=email:copy
# Copy issuer details
# issuerAltName=issuer:copy
# DER hex encoding of an extension: beware experts only!
# obj=DER:02:03
# Where 'obj' is a standard or added object
# You can even override a supported extension:
# basicConstraints= critical, DER:30:03:01:01:FF
[ crl_ext ]
# CRL extensions.
# Only issuerAltName and authorityKeyIdentifier make any sense in a CRL.
# issuerAltName=issuer:copy
authorityKeyIdentifier=keyid:always
[ proxy_cert_ext ]
# These extensions should be added when creating a proxy certificate
# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.
basicConstraints=CA:FALSE
# This is typical in keyUsage for a client certificate.
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment
# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
# This stuff is for subjectAltName and issuerAltname.
# Import the email address.
# subjectAltName=email:copy
# An alternative to produce certificates that aren't
# deprecated according to PKIX.
# subjectAltName=email:move
# Copy subject details
# issuerAltName=issuer:copy
# This really needs to be in place for it to be a proxy certificate.
proxyCertInfo=critical,language:id-ppl-anyLanguage,pathlen:3,policy:foo
####################################################################
[ tsa ]
default_tsa = tsa_config1 # the default TSA section
[ tsa_config1 ]
# These are used by the TSA reply generation only.
dir = ./demoCA # TSA root directory
serial = $dir/tsaserial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/tsacert.pem # The TSA signing certificate
# (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply
# (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
signer_digest = sha256 # Signing digest to use. (Optional)
default_policy = tsa_policy1 # Policy if request did not specify it
# (optional)
other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional)
digests = sha1, sha256, sha384, sha512 # Acceptable message digests (mandatory)
accuracy = secs:1, millisecs:500, microsecs:100 # (optional)
clock_precision_digits = 0 # number of digits after dot. (optional)
ordering = yes # Is ordering defined for timestamps?
# (optional, default: no)
tsa_name = yes # Must the TSA name be included in the reply?
# (optional, default: no)
ess_cert_id_chain = no # Must the ESS cert id chain be included?
# (optional, default: no)
ess_cert_id_alg = sha1 # algorithm to compute certificate
# identifier (optional, default: sha1)
[insta] # CMP using Insta Demo CA
# Message transfer
server = pki.certificate.fi:8700
# proxy = # set this as far as needed, e.g., http://192.168.1.1:8080
# tls_use = 0
path = pkix/
# Server authentication
recipient = "/C=FI/O=Insta Demo/CN=Insta Demo CA" # or set srvcert or issuer
ignore_keyusage = 1 # potentially needed quirk
unprotected_errors = 1 # potentially needed quirk
extracertsout = insta.extracerts.pem
# Client authentication
ref = 3078 # user identification
secret = pass:insta # can be used for both client and server side
# Generic message options
cmd = ir # default operation, can be overridden on cmd line with, e.g., kur
# Certificate enrollment
subject = "/CN=openssl-cmp-test"
newkey = insta.priv.pem
out_trusted = apps/insta.ca.crt # does not include keyUsage digitalSignature
certout = insta.cert.pem
[pbm] # Password-based protection for Insta CA
# Server and client authentication
ref = $insta::ref # 3078
secret = $insta::secret # pass:insta
[signature] # Signature-based protection for Insta CA
# Server authentication
trusted = $insta::out_trusted # apps/insta.ca.crt
# Client authentication
secret = # disable PBM
key = $insta::newkey # insta.priv.pem
cert = $insta::certout # insta.cert.pem
[ir]
cmd = ir
[cr]
cmd = cr
[kur]
# Certificate update
cmd = kur
oldcert = $insta::certout # insta.cert.pem
[rr]
# Certificate revocation
cmd = rr
oldcert = $insta::certout # insta.cert.pemopenssl.cnf
Buat root ca.key
openssl genrsa -out ca.key 4096Buat root ca.crt
openssl req -new -key ca.key -out ca.crt -config openssl.cnf -x509 -days 365Buat sub CA key stembayo.id
openssl genrsa -out stembayo.id.key 4096Buat sub CA CSR stembayo.id
openssl req -new -key stembayo.id.key -out stembayo.id.csr -config openssl.cnf -extfile openssl.cnf -extensions v3_reqTTD sub CA
openssl ca -config openssl.cnf -in stembayo.id.csr Database (MariaDB)
Install mariadb
sudo apt update
sudo apt install -y mariadbSecure setup mariadb
gunakan Skills39 sebagai password root
sudo mysql_secure_installationWeb Server (Nginx)
Instalasi
sudo apt update
sudo apt install -y nginxEdit /etc/nginx/nginx.conf
# Aktifkan baris ini
server_names_hash_bucket_size 64;/etc/nginx/nginx.conf
Virtual Host (lnx.stembayo.id)
Buat directory
sudo mkdir -p /var/www/lnx.stembayo.id/
sudo chown -R $USER:$USER /var/www/lnx.stembayo.id/
sudo chmod -R 755 /var/www/lnx.stembayo.id/Buat file index.html
nano /var/www/lnx.stembayo.id/index.html<html>
<head>
<title>LNX</title>
</head>
<body>
<h1>Hello :)</h1>
</body>
</html>/var/www/lnx.stembayo.id/index.html
Buat virtual host
sudo nano /etc/nginx/sites-available/lnx.stembayo.idserver {
listen 80;
server_name lnx.stembayo.id;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name lnx.stembayo.id;
ssl_certificate /ssl/stembayo.id/stembayo.id.pem;
ssl_certificate_key /ssl/stembayo.id/stembayo.id.key;
root /var/www/lnx.stembayo.id;
index index.html;
location / {
try_files $uri $uri/ =404;
}
}/etc/nginx/sites-available/lnx.stembayo.id
Aktifkan virtual host
sudo ln -s /etc/nginx/sites-available/lnx.stembayo.id /etc/nginx/sites-enabled/Cek konfigurasi
sudo nginx -tRestart nginx
sudo systemctl restart nginxBasic Auth
Install apache2-utils
sudo apt update
sudo apt install apache2-utilsBuat user baru
nama: competitor
pass: Skills39
sudo htpasswd -c /etc/nginx/.htpasswd userNote: -c hanya digunakan saat pertama kali
Buat directory
sudo mkdir -p /var/www/basic-auth.stembayo.id/
sudo chown -R $USER:$USER /var/www/basic-auth.stembayo.id/
sudo chmod -R 755 /var/www/basic-auth.stembayo.id/Buat file index.html
nano /var/www/basic-auth.stembayo.id/index.html<html>
<head>
<title>Basic Auth</title>
</head>
<body>
<h1>Basic Auth</h1>
</body>
</html>/var/www/basic-auth.stembayo.id/index.html
Buat virtual host (basic-auth.stembayo.id)
sudo nano /etc/nginx/sites-available/basic-auth.stembayo.idserver {
listen 80;
server_name basic-auth.stembayo.id;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name basic-auth.stembayo.id;
ssl_certificate /ssl/stembayo.id/stembayo.id.pem;
ssl_certificate_key /ssl/stembayo.id/stembayo.id.key;
root /var/www/basic-auth.stembayo.id;
index index.html;
auth_basic "Restricted Content";
auth_basic_user_file /etc/nginx/.htpasswd;
location / {
try_files $uri $uri/ =404;
}
}/etc/nginx/sites-available/basic-auth.stembayo.id
Aktifkan virtual host
sudo ln -s /etc/nginx/sites-available/basic-auth.stembayo.id /etc/nginx/sites-enabled/Cek konfigurasi
sudo nginx -tRestart nginx
sudo systemctll restart nginxReferensi: https://www.digitalocean.com/community/tutorials/how-to-install-nginx-on-ubuntu-22-04
Wordpress
...
Mail Server (Dovecot)
...
Web Mail (Roundcube)
...
Member discussion